

What does oVirt offer that proxmox doesn’t? I’m asking because I want to move an ESXi server to another hypervisor, I’m 90% sure it’ll be Proxmox, but I’d like to know my options.
I take my shitposts very seriously.


What does oVirt offer that proxmox doesn’t? I’m asking because I want to move an ESXi server to another hypervisor, I’m 90% sure it’ll be Proxmox, but I’d like to know my options.
No idea. It depends on what software it uses for network configuration, and how that software handles DHCP failure. I use NetworkManager and I’ve never gotten an APIPA address.
I’ve never used a pi, but it should be possible to mount the root partition and edit the /etc/network/interfaces or /etc/dhcpcd.conf file, or /etc/NetworkManager/conf.d/* if you have NetworkManager (systemctl status NetworkManager to check).
You should also make sure that sshd is listening for connections from any address (0.0.0.0 and ::).
oops, fixed. Caffeine withdrawal is hell.
Most modern NICs can auto-negotiate the Rx/Tx circuits on either kind of cable, but I’m not sure about RPi.
Give each device a static address, and set the default gateway to whatever’s on the other end of the cable. You might need a crossover cable, but most NICs can work using a straight-through.
E.g. set the laptop’s address to 169.254.1.1/16 and default gateway to 169.254.1.2, and the RPi’s address to 169.254.1.2/16 and default gateway to 169.254.1.1. They should be able to talk to each other then.
If those addresses seem familiar - Windows uses the 169.254.0.0/16 subnet to automatically assign random addresses if DHCP fails, so that if there are several computers in the subnet, they’ll at least have addresses that can talk to each other. It’s called APIPA in Windows, and Zeroconf in the Unixverse.


I tried Tailscale once, but it introduced some massive latency because apparently I got connected to my machine through a gateway in Frankfurt. It was the Tailscale Funnel service though, so maybe that’s not what I needed.
Also, are any of the services you listed end-to-end encrypted?


Proxmox VE on a machine that I got almost for free. Intel i3-4160, 10GB RAM, 240GB SSD for the OS, and a non-redundant 1T HDD for storage. The only things I paid for are a second NIC and an 8GB RAM stick.
PVE is running a pfSense VM, and a bunch of Debian containers:
All internet traffic goes through the pfSense VM. Unfortunately the ISP has put me behind CGNAT and disabled bridge mode, so my internet-facing things (mostly Wireguard and SSH) are pretty much crippled. Right now my best no-cost option is to use Twingate, but I don’t trust it to handle anything other than SSH.
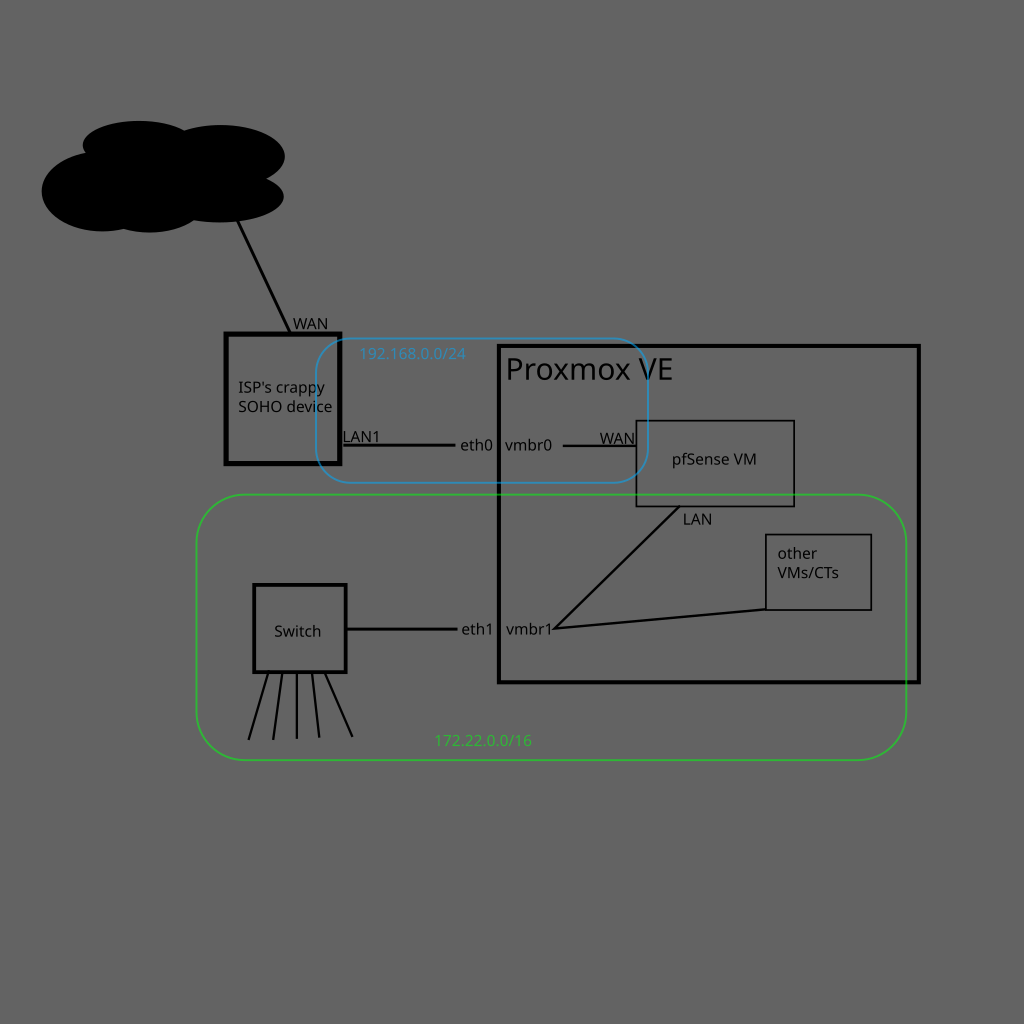
That was informative, thanks.
What about wireless devices, are they on the LAN side too?
If I may ask, how exactly do you use OPNsense? Is it a gateway between the WAN and LAN interfaces, or do you just use it for the LAN-facing services?


Absolutely anything can be turned into a NAS, as long as you’re aware of your own needs and the hardware’s capabilities. A NAS is just a computer with some specific requirements.
When I first built my NAS, it only used parts that I got for free. A cheap micro ATX board with only two RAM slots, an i3-4160 CPU, 2x2G RAM, a worn-out SSD, and a 1T HDD. It couldn’t run something like TrueNAS, but it was enough for Proxmox and some Alpine containers running services like Samba, Transmission, Wireguard, and a small Debian VM for me to fuck around with. The single storage disk means there is no redundancy, so I only store replaceable data on it, like TV shows and installers.
There are many hardware-focused channels on video platforms that offer guides for budget home servers. Wolfgang’s Channel is good, and Hardware Haven and Raid Owl just finished a competition of building a sub-$200 home lab.


Then just get a pair of hard drives and put them in RAID 1. I use a NAS with a single hand-me-down 5600 RPM HDD and the bandwidth is absolutely fine.
Seconded. ZFS needs to see the physical devices, so hardware RAID is out. It implements a RAID-5-like parity-based software solution called RAID-Z, and is capable of disk mirroring.
It can work with hardware RAID or with a single physical disk, but don’t expect it to last for a long time, and definitely don’t use it beyond testing.


As someone who used Checkmk Raw (the free edition) and stopped because it’s an absolute bastard to set up, I’m going to recommend Zabbix.
I’ll specify. Installing Checkmk’s agent on the servers was fine, but service discovery is completely unreliable (I could never get through a full discovery before it just hung on something unknown) and the web GUI is very difficult to navigate. Unfortunately most of the documentation only covers the paid version, and community support is pretty bad.
Switching to Zabbix was almost plug-and-play by comparison.
You mean Wireshark? It’s possible. You might even capture the DHCP exchange.
The two best programs for the job are
nmapandarp-scan.Nmap is like ping on steroids. You can use it for network discovery, port scanning, fingerprinting, and basic pentesting. As long as the pi can talk to the computer,
nmapwill sniff it out.ARP-scan works on the data link layer to identify hosts using ARP. It should be able to return the IP address of all ethernet devices even if they end up in different subnets. It took me a little over two minutes to scan a /16 subnet with one retry and 0.1 second timeout.
If you are really concerned about the pi’s address, you should run a local DHCP server on the laptop.
dnsmasqfor Linux and Mac, but I have no idea what to use on Windows (other than a VM bridged to the ethernet interface).